
Security in Mobile Devices
Security in Mobile Devices
Have you ever wondered about your cell phone's security? Are you aware of the risks that surround you? Overlooking such an issue may threaten high amounts of data.

The revolution of mobile technologies is an unprecedented event, and since they appeared for the very first time, their development hasn't stopped growing. However, as in everything related to technology and computing, parallel to its positive development, there's also a dark side to it, as security threats associated to mobile devices have also grown. Since 2004, when the first malicious code for this type of terminals appeared, the tendency hasn't stopped increasing.
The increase of possibilities and capacities that mobile devices have associated currently implies likewise higher security risks. It is very important for users to be aware of the importance of security in mobile devices and the dangers their inappropriate use can entail.
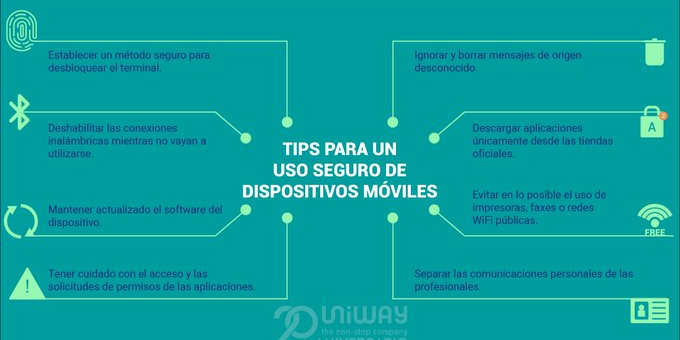
It is convenient to follow the following tips:
- Set a safe method to unlock the terminal, for instance using safe passwords (Use facial and biometric recognition).
- Get rid of message preview notifications and take every single measure when your phone is not at reach.
- Disable wireless connections (WiFi, Bluetooth, etc.) and all of those that are not necessary as long as you don't use them.
- Keep your device software updated and use approved security configuration.
- Be careful with the access and permission requests of the applications that get executed in your smartphone.
- Ignore and delete messages (SMS, MMS or others) coming from an unknown source that invite you to download any content or access websites.
- Activate access through PIN to Bluetooth connections and configure the device in stealth mode. Don't accept connections from unknown devices.
- Download applications just from the official stores. Don't download software from unreliable sites under any circumstances.
- Avoid to jailbreak* or root* the terminal, since it may compromise or reduce sustantially the phone's security despite the temptation to access specific applications or services.
- Use a virtual private network to protect data traffic. It is always a good practice to avoid possible monitoring by intruders.
- Avoid as much as possible using printers, faxes or public WiFi networks, such as those offered in hotels or airports, unless you have the necessary tools to ensure your communications.
- Digital cameras add GPS coordenates in the information of the images taken, so it is appropriate to limit sharing images over the network or using applications that delete said information.
- Separating personal communications from professional ones is a good security practice. To manage sensitive information, use only technically approved solutions.
Backup
Bear in mind that ransomware attacks are very common nowadays and they were still one of the most relevant threats in 2020, affecting 50% of the companies in Spain. The chances of suffering one are pretty high! Despite all protections and precautions you may have taken, they can still get in and block your information. If you end up paying an extortion, you become a weak target and you will surely be attacked again in the coming future.
With a correct periodic backup policy, not only will you avoid losing information in case of mobile device loss or theft (smartphone, laptop...), but also avoid information theft in those cyberattacks that will block or encrypt data access. Having your data copied once in a while in a remote location, will enable you to recover those data easily and quickly affecting your company, your work and your clients as little as possible. Of course without paying for an unnecessary blackmail that will negatively affect your corporate image.
It is important to use safe devices and locations to store those backups. Information recovery at any time must be absolutely guaranteed. Carrying out tests or drills to guarantee backup integrity must be an essential task within your security policy.
- Jailbreak. Hacking Apple devices to be able to add third party applications and features.
- Rooting. Hacking Android devices so that any application may get full access to the system and carry out tasks that it couldn't perform otherwise.





