
Cybersecurity analysis - Pentesting
to detect vulnerabilities in your systems
Pentesting consists of performing an intrusion test on a computer system or environment to evaluate its security level and detect its vulnerabilities.
At Uniway we use specialized tools and techniques that simulate real hacker attacks.
The objective is to identify and exploit the weaknesses of the system in order to correct them and prevent possible cyber-attacks; preserving each of the evaluations made and allowing the monitoring and evolution of security in the technological park.
It is a very useful technique for companies and organizations because it provides an analysis of the real state of their systems in terms of cybersecurity and implement the necessary measures to protect them.


What we do?
We proactively examine your cybersecurity
to identify your vulnerabilities and fix them 24x7

Continuous risk inspection
We continuously monitor the exposure of your systems on the network to anticipate possible cyber-attacks.

Effective information
We provide a detailed description of your vulnerabilities in an accessible language, focused on the real impact to your security.

Vulnerability solution
We provide you with all the information to solve your vulnerabilities. You can count on our cybersecurity experts to make the necessary corrections.
Assess your risks, protect your business and work with confidence
Immediate availability
Start at any time with zero effort, paying only for the use with a simplified process without complex installations.
Full integration
Analyze your systems no matter what technical environment they are in. Our SaaS product allows multiple integrations in the cloud.
Proactive approach
We perform periodic diagnostics detecting security holes in your most exposed systems before cyber-attacks occur.
How we do it?

Cloud-based Vulnerability Scanner
We detect and assess
We simplify the process as much as possible for you, we only need you to provide us with the systems you want to assess. From there, our specialists take care of detecting the vulnerabilities that may exist. Uniway Pentesting adapts to increasingly complex environments and diverse sets of assets and provides reports with understandable results and classified according to their level of criticality without the need for prior technical knowledge.

Cloud-based Vulnerability Scanner
We detect and assess
We simplify the process as much as possible for you, we only need you to provide us with the systems you want to assess. From there, our specialists take care of detecting the vulnerabilities that may exist. Uniway Pentesting adapts to increasingly complex environments and diverse sets of assets and provides reports with understandable results and classified according to their level of criticality without the need for prior technical knowledge.
Complete Surveillance
We carry out projects tailored to your needs for the complete coverage of your systems, both internal and external; thus ensuring the active and passive protection of your company continuously against hacker attacks and internal risks that may exist and we offer you the availability of hiring an ethical hacking project (White Hacking / Network Team).


Complete Surveillance
We carry out projects tailored to your needs for the complete coverage of your systems, both internal and external; thus ensuring the active and passive protection of your company continuously against hacker attacks and internal risks that may exist and we offer you the availability of hiring an ethical hacking project (White Hacking / Network Team).

Related products
Choose the modality that best suits your company's needs
Pentesting Punctual analysis
Pentesting of up to 3 external IPs with technical and executive reports; with three types of alert swe according to their criticality and corrective proposals for vulnerabilities.
From: 300,00 €
Continuous Pentesting
Monthly pentesting of up to 3 external IPs, extendable to internal IPs, with technical and executive reports; with three types of alerts according to their criticality and correction proposals for the vulnerabilities detected and other advantages.
From: 160,00 €
Customized plan
Pentesting tailored to the specific needs of your systems; with pre-developed integrations; continuous monitoring and support projects and support to your cybersecurity for both active and passive protection of your company.
Preguntas Frecuentes

Pentesting
We perform monthly pentesting for up to 3 external IPs, providing regular security analysis.
Título Hovered
Descripción hovered

Technical - executive reports
With three types of alerts according to their criticality, with a proposal to correct the vulnerabilities detected.
Título Hovered
Descripción hovered

Storage of reports
Specially generated for possible evolution analysis and management, guaranteeing security traceability.
Título Hovered
Descripción hovered

Access to the Tenable Console
For customization of tool data, ensuring a user experience tailored to your needs.
Título Hovered
Descripción hovered

Technical Support
Immediate and reliable for the resolution of the incidences encountered, minimizing any interruption.
Título Hovered
Descripción hovered

Service scalability
We offer the possibility of extending the analysis to all your internal IPs, guaranteeing complete security coverage.
Título Hovered
Descripción hovered

Support projects
Designed for active and passive protection of your company, and we offer the option of hiring an ethical hacking project.
Título Hovered
Descripción hovered

Meeting the requirements
We comply with CERT, NIST, DISA STIG, DHS CDM, FISMA, PCI DSS, HIPAA/HITECH standards, guaranteeing the highest levels of security.
Título Hovered
Descripción hovered
With the service offered, your company will have complete visibility of all its network assets and the risks to which they are exposed; making it possible to quickly detect and respond to critical vulnerabilities, proactively disrupting attack paths.
Our service assesses your vulnerabilities regardless of the hyperscale used by your systems (AWS, Azure, Google Cloud, etc). We securely perform vulnerability analysis of your systems without intrusiveness on your platform, ensuring your privacy and the security of your information.
Our service assesses your vulnerabilities regardless of the hyperscale used by your systems (AWS, Azure, Google Cloud, etc). We securely perform vulnerability analysis of your systems without intrusiveness on your platform, ensuring your privacy and the security of your information.
The service provided by Uniway meets the requirements of international cybersecurity regulations, aligned with CERT, NIST, DISA STIG, DHS CDM, FISMA, PCI DSS, HIPAA/HITECH compliance.
Possible scenarios
Integration alternatives according to your systems
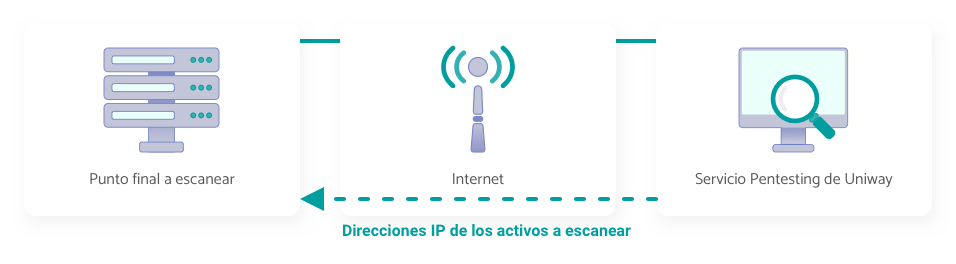
Wide area network systems
We simulate a wide area network (WAN) attack to find and exploit vulnerabilities from a public perspective. The objective is to assess the resilience of the network against possible external threats and improve protection measures, as it focuses on systems directly exposed to the Internet. The service runs automatically.
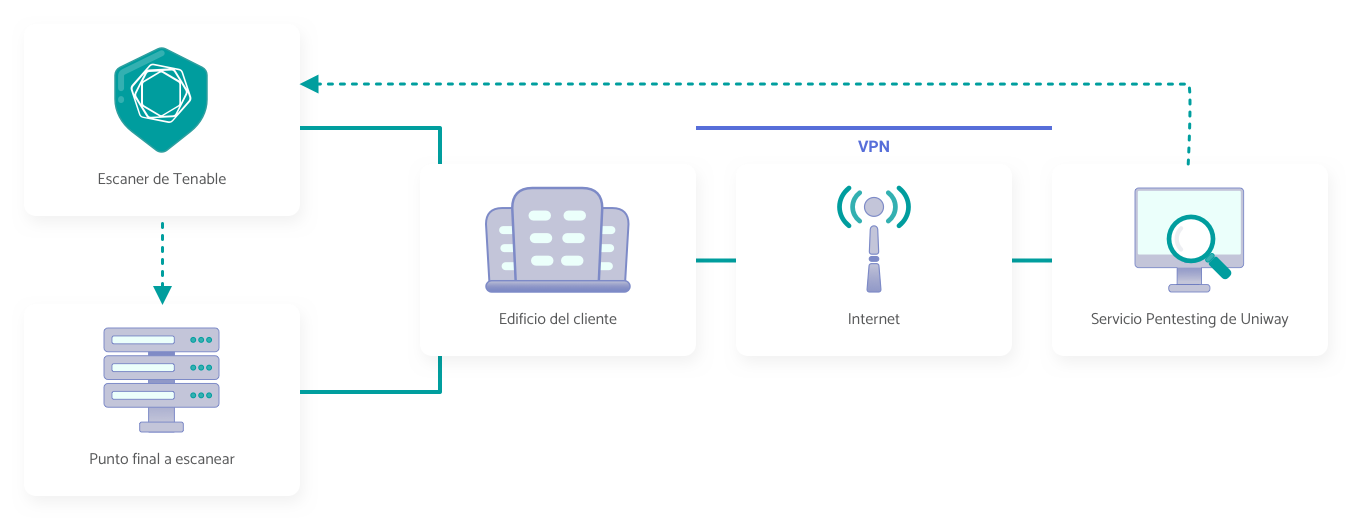
Local network systems
We simulate an attack on a local area network (LAN) to find and exploit vulnerabilities from an internal perspective. The objective is to assess the resilience of the network against potential insider threats and improve protection measures, as it focuses on the evaluation of corporate security.
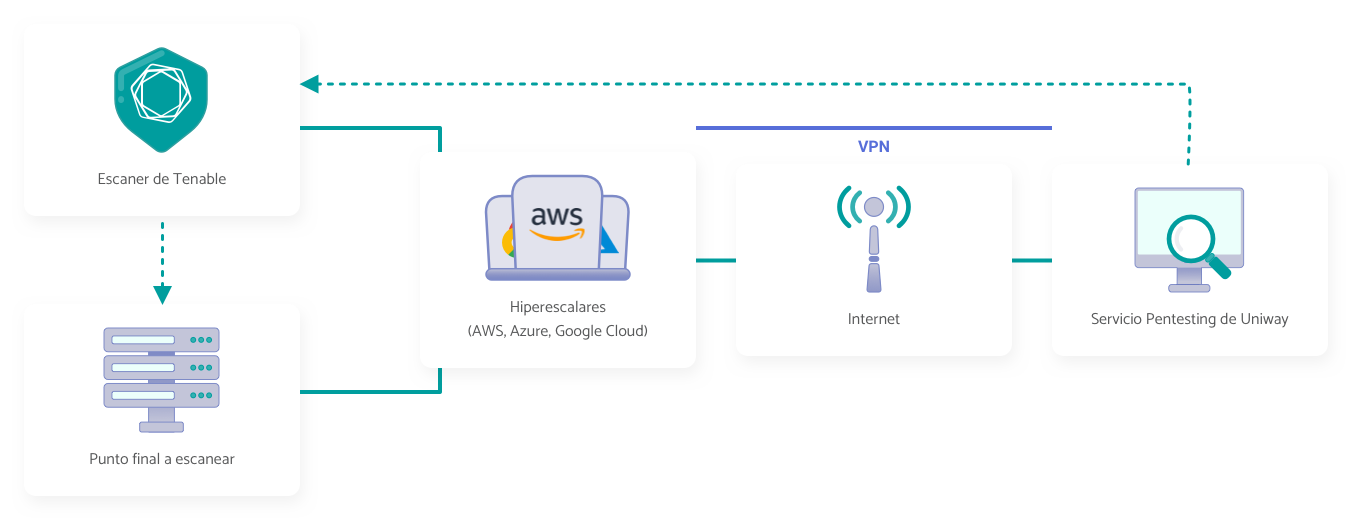
Cloud Network
We simulate an attack on a cloud network to find and exploit vulnerabilities from a global perspective. The objective is to evaluate the resilience of the network against possible external and internal threats and to improve protection measures, as it focuses on hyperscale systems or in the Cloud.
Articles and videos that may be of interest to you







